Trying a terminal connection
In Part 1 we found out that the camera runs over Linux, but there are no SSH port open for a remote shell connection. So I'll try something more hardcore: Let's disassemble the camera
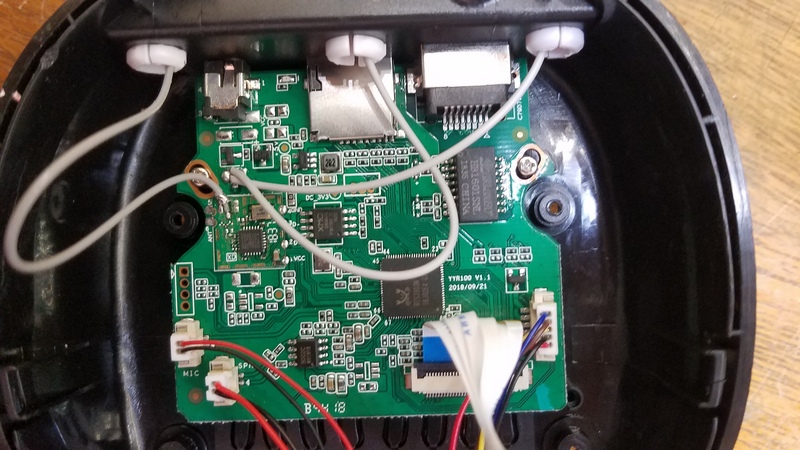
The first thing I noticed is the low quality of the antennas connections. Just three simple cheap wires, spread all over the camera enclosure, attached to the PCB by large blobs of solder... Not a good RF design decision...
Also, there's 3 antennas, but two of them are connected to the same point on PCB, while the third one is connected to the a segregated PCB module. This may indicate that the camera has 2 different WiFi interfaces
We also see two groups of unused pins that could be, maybe, debug ports left by the developers. I've marked them on the next picture
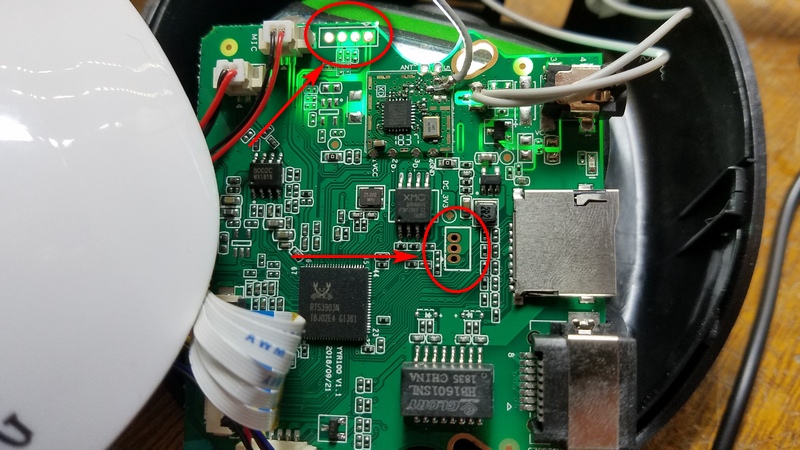
So, let's find out if we can use these as a serial port.
The first one, on the top of the picture, seems to be connected to the second PCB, which is connected to the antenna. That's probably a dedicated processor for the WiFi configuration. The second group of pins, however, seems to be connected to a large processor, which is probably the main processor in this PCB. I'll start with this one.
It contains 3 pins, so, for a serial port, we would need them to be, at least RX, TX and some power, probably GND. By using a bright light under the board I can see how they are connected:
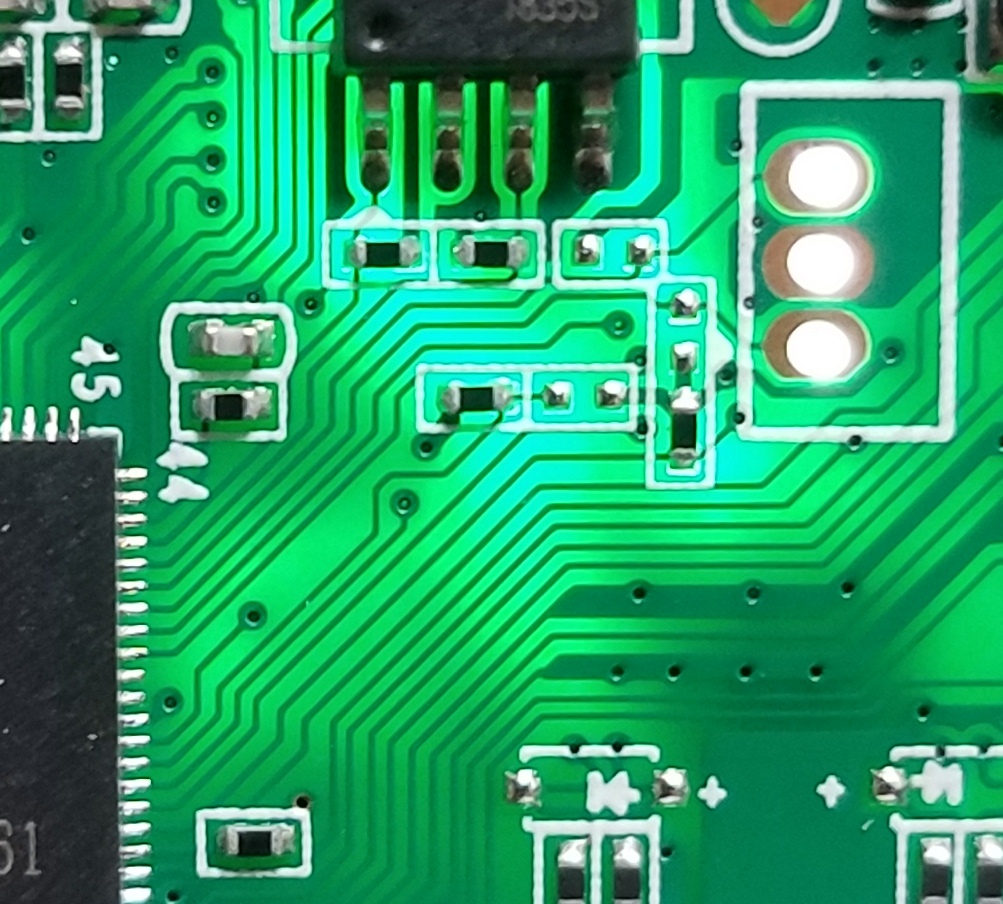
Now we can see clearly: The center connector is connected to the PCB ground. The other two are connected to the main processor.
I tried googling the numbers on the processor, but could not find any datasheets, so I've checked those pins on the oscilloscope and, yes, one of the pins seems to be transmitting data:
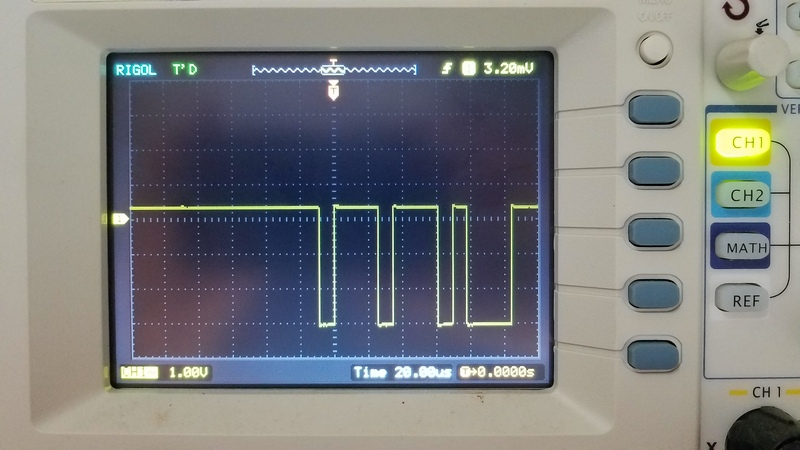
So, here we found out that this is, very probably, a serial port transmitting data, and it works at 3.3V.
I could even try to find out the data rate (speed) used by this port using the oscilloscope, but is way easier to simply guess that on a terminal software. So I soldered these 3 pins to a cable, connected it to my computer, launched TeraTerm and... A lot of garbage started appearing on the screen. It seemed that I was really receiving data from the camera. A few trials with the connection speed and Voilà! I am now receiving consistent data from the camera:

Now we have a lot of information to process. The camera really runs on Linux. We can see the exactly version, the bootloader it uses, some information about the processor, etc.
But the most interesting is this. After the camera finished its startup process, I could type on my terminal connection. So, maybe I could send commands to the camera via the terminal connections. Let's try:

Soooo... YES. We have fully access to the Linux shell via this debug port, and the user is... ROOT
That really opens a lot of interesting opportunities. I'll check on them on Part 3